
How is it possible to hack Gmail multifactor authentication? Access from apps plus social engineering.
Hackers from Russia posing as representatives of the U.S. State Department, targeting prominent scholars and critics of Russia. The attack was carried out using a technique of «sophisticated and personalized social engineering», according to BleepingComputer.
Between April and early June, hackers sent out carefully crafted phishing messages that aimed to convince recipients to create and share passwords for apps. These programs, in turn, provided access to Google accounts. This way, two-factor authentication (2FA) was bypassed, as users themselves provided the app with access to Gmail.
Security researchers from the Google Threat Intelligence Group (GTIG) have tracked down the cybercriminal known as UNC6293. They believe that the hacker is sponsored by the Russian state and may be connected to the APT29 group, run by Russia’s foreign intelligence service. It is also known by the names NobleBaron, Nobelium, Cozy Bear, CozyDuke, Midnight Blizzard and has been operating since at least 2008. Its targets include government networks, research institutes, and think tanks.
The research team The Citizen Lab investigated the incident of the UNC6293 phishing campaign targeting information operations expert Keir Giles. The attack began with an email signed by Claudie S. Weber, allegedly from the U.S. Department of State in which Giles was invited to a «private online conversation».
Although the message came from a Gmail account, the cc line contains several @state.gov email addresses, including that of Claudie S. Weber, who gives the email a more formal look. Researchers have not found any Claudia S. Weber in the State Department.
«We believe the attacker is aware that the State Department’s email server is apparently configured to accept all messages and does not send bounce notifications even if the address does not exist», — The Citizen Lab says
After several emails, Giles expressed interest, but said he might not be available on the day in question. The attacker then invited him to join the Department of State’s «MS DoS Guest Tenant» platform, «which would allow him to easily attend future meetings, no matter when they occurred».
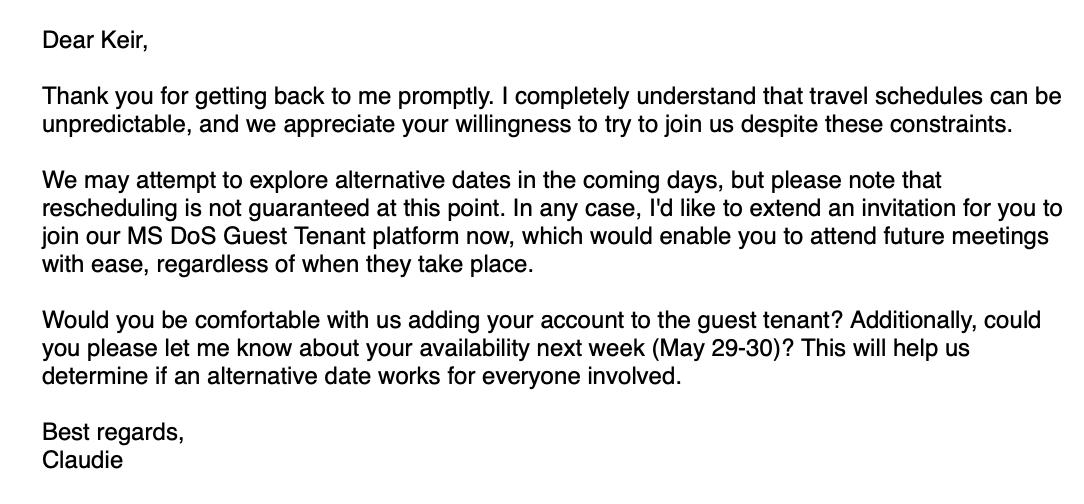
Giles agreed and received a PDF detailing how to create a password for a separate app with access to a Google account, which was supposedly needed to register a guest user on the platform.
The access code to the app was to be passed to «DoS administrators in the United States to add the external user to the O365» guest tenant. This was explained in the instructions for an alternative solution that allegedly provides secure communication through the platform between DoS employees in the US and external users with Gmail accounts.
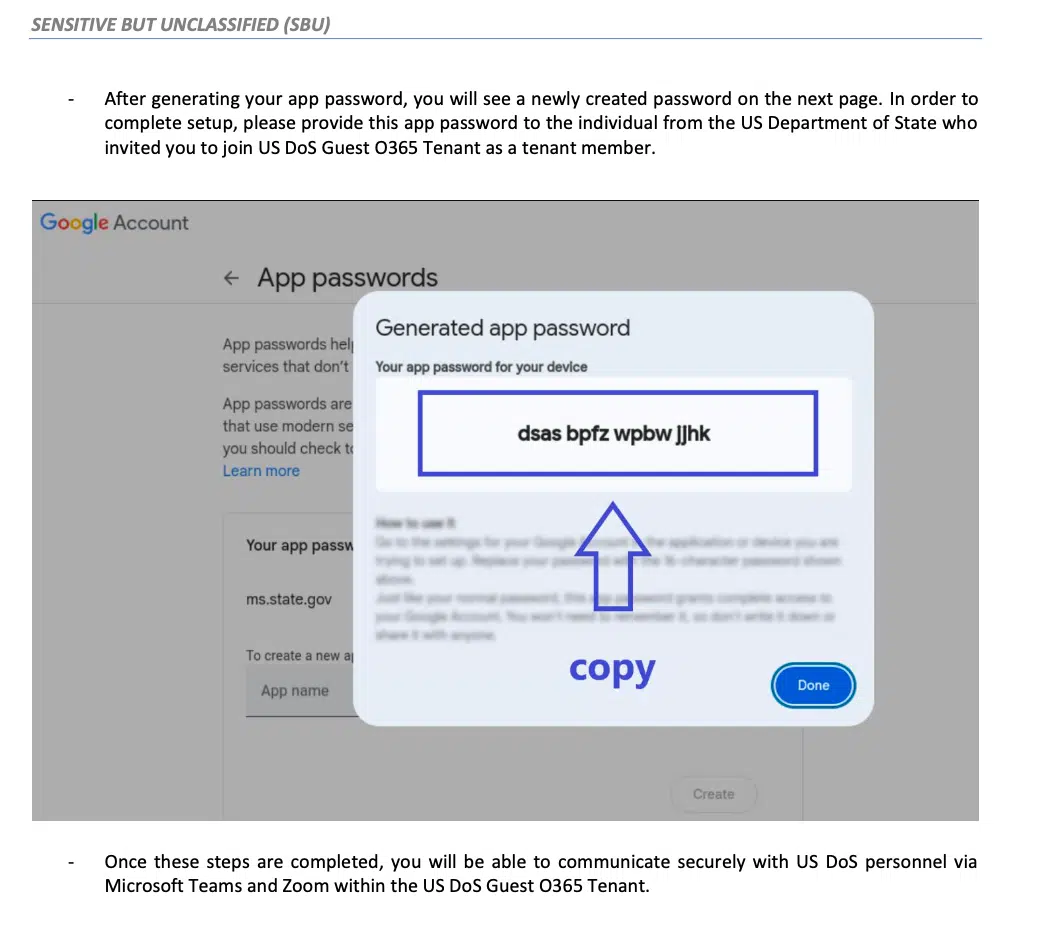
Psychologically, the target believes they are creating and sharing an app password for secure access to the State Department platform, when in fact they are giving the attacker full access to their Google account.
Between April and June, GTIG identified two campaigns, one that relied on State Department-related topics and the other that used decoys related to Ukraine and Microsoft. Both campaigns had resident proxy servers and virtual private servers in their infrastructure, which allowed the attacker to remain anonymous while logging into the compromised accounts.
The social engineering campaigns observed by The Citizen Lab and GTIG were sophisticated and relied on numerous fake identities, accounts, and other data and techniques to create the illusion of authenticity. To protect yourself from sophisticated attackers, Google recommends signing up for the Advanced Protection Program, which enhances your account security measures and prevents you from creating a password for such apps or logging in without a login.

Spelling error report
The following text will be sent to our editors: