
On May 22, hackers found a vulnerability in the business logic of the Cetus protocol smart contract targeting CLMM pools The Concentrated Liquidity Market Maker model increases the efficiency of capital use within a liquidity pool by minimizing slippage. This allows for more efficient use of capital as liquidity is concentrated where the most trades occur. Cetus is the largest decentralized exchange (DEX) on the Sui blockchain and the largest liquidity aggregator on the network
The Concentrated Liquidity Market Maker model increases the efficiency of capital use within a liquidity pool by minimizing slippage. This allows for more efficient use of capital as liquidity is concentrated where the most trades occur. Cetus is the largest decentralized exchange (DEX) on the Sui blockchain and the largest liquidity aggregator on the network It is software that collects market orders from different platforms into one stream and sends it to liquidity providers, where it is matched, and if the stated price of the seller and the buyer match, the transaction is executed.. Due to the bug found cybercriminals managed to extract $223 million from Cetus Protocol. This led to severe consequences: liquidity pools were almost empty, and trading stopped, tokens on the Sui blockchain began to lose value, USDC stablecoin lost its peg to the dollar. The value of the Sui network token and related coins continues to fall. What awaits the network next: oblivion or can it still be saved by recovery?
It is software that collects market orders from different platforms into one stream and sends it to liquidity providers, where it is matched, and if the stated price of the seller and the buyer match, the transaction is executed.. Due to the bug found cybercriminals managed to extract $223 million from Cetus Protocol. This led to severe consequences: liquidity pools were almost empty, and trading stopped, tokens on the Sui blockchain began to lose value, USDC stablecoin lost its peg to the dollar. The value of the Sui network token and related coins continues to fall. What awaits the network next: oblivion or can it still be saved by recovery?
Content
Chronology of the Cetus Protocol hack
- 10:30:50 UTC — The exploit of the pricing mechanism began through anomalous transactions. The attackers exploited a critical overflow vulnerability in the logic of the Cetus automated market maker. This allowed the attackers to manipulate liquidity calculations and withdraw significant funds from the platform’s liquidity pools.
- 10:40:00 UTC — an anomaly is detected in the pool behavior by the monitoring systems.
- 10:53:00 UTC — The source of the attack is identified by the Cetus team and shared with members of the Sui ecosystem.
- 10:57:47 UTC — The main CLMM pools have been shut down to prevent further losses.
- 11:20:00 UTC — all relevant smart contracts are globally disabled.
- 12:50:00 UTC — Sui validators began voting to refuse to service transactions signed with the attacker’s addresses, and after the number of votes exceeded 33%, the validators effectively froze these addresses. Thus, the hackers did not get $174 million out of $223 million.
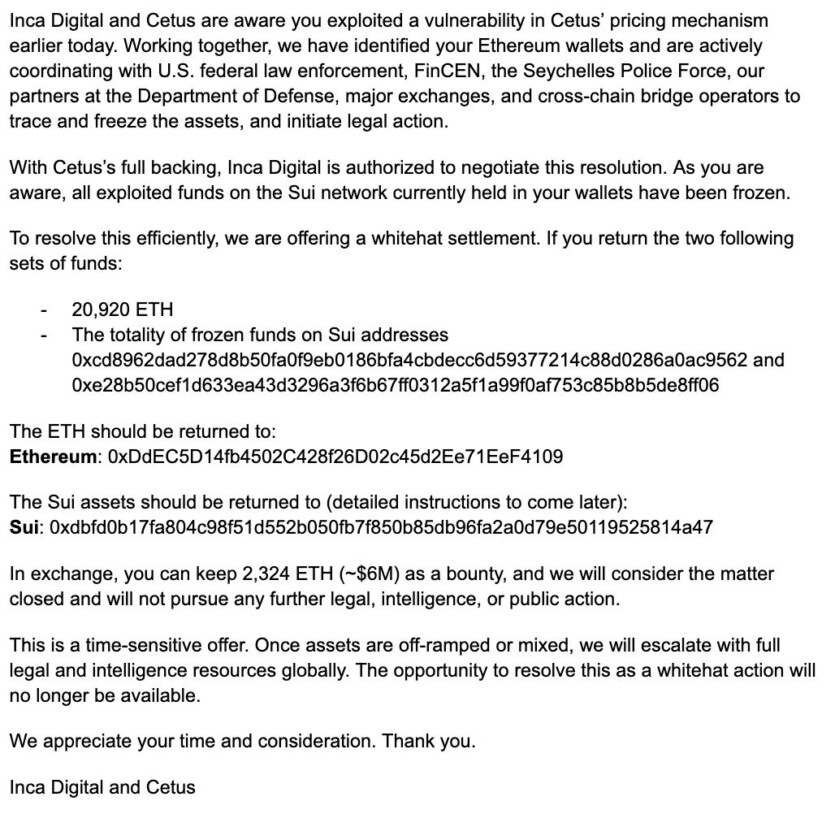
- 18:04:07 UTC – messages for online negotiations was sent to the attacker. The hackers were offered $6 million for the return of the invested funds.
- 18:15:28 UTC — The vulnerable contract has been patched and updated (but not yet restarted).
How it happened
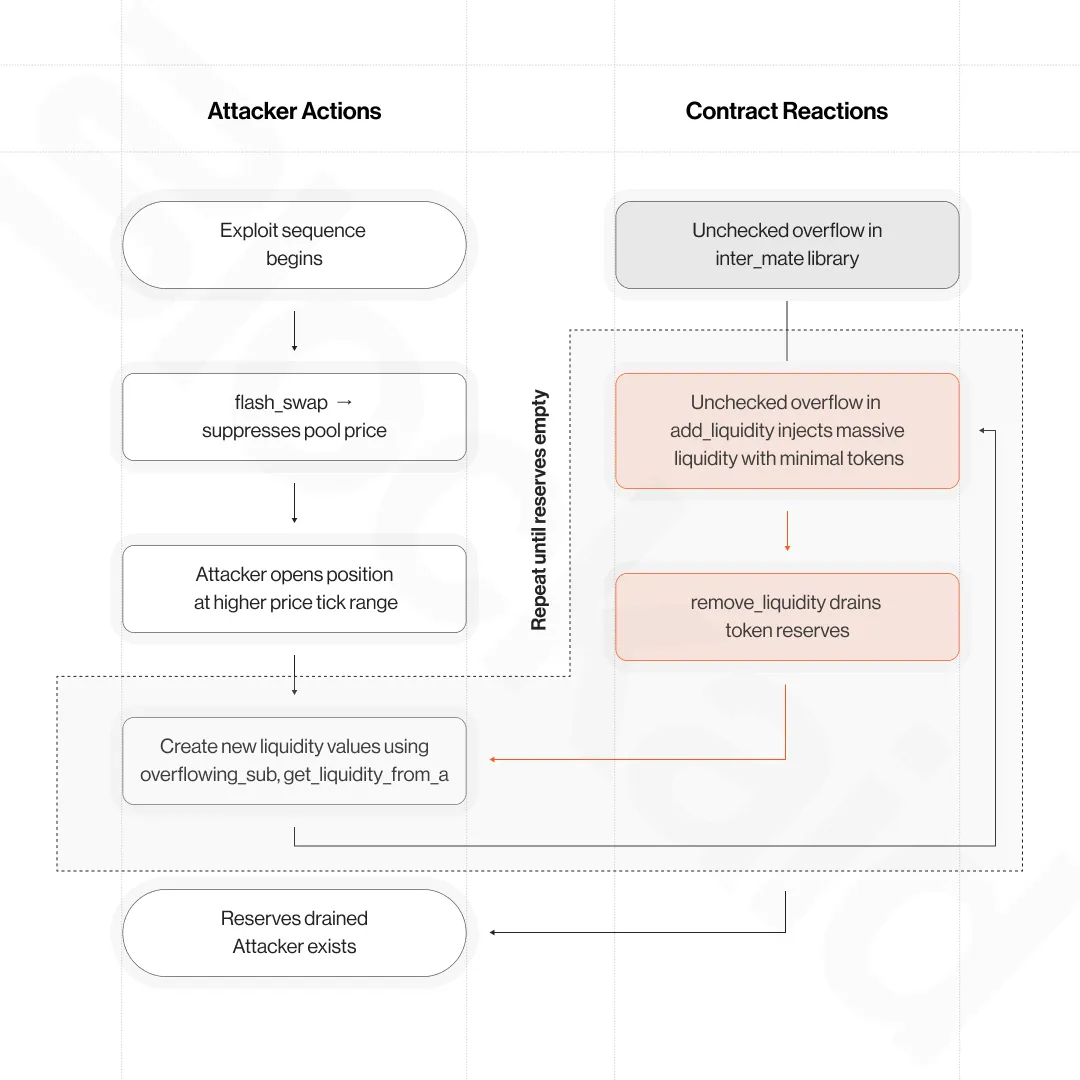
The attacker exploited a vulnerability in the CLMM contract that arose from a flaw in the inter_mate open-source library used in Cetus smart contracts. Here’s how the exploit happened:
-
The attacker took advantage of the instant exchange function (flash_swap) to temporarily lower prices in the liquidity pools. This allowed him to create favorable conditions for further actions.
-
The hacker then opened positions in the range where prices were higher, which allowed him to gain an advantage when adding liquidity.
-
In the function add_liquidity there was no proper check for overflow numbers. The attacker exploited this to introduce an artificially high amount of liquidity, but without actually providing the actual number of tokens.
-
Thanks to the fake liquidity, the attacker was able to repeatedly withdraw liquidity, receiving real tokens from the pools.
-
The attacker repeated these actions using incorrect calculations in other functions (overflowing_sub, get_liquidity_from_a). He made millions of dollars through this substitution.
By exploiting the shortcomings of automatic calculations, the attacker overwhelmed the calculations of how much to pay to add liquidity to the various pools. This allowed him to pay at a significantly reduced rate and liquidate — at the original rate.
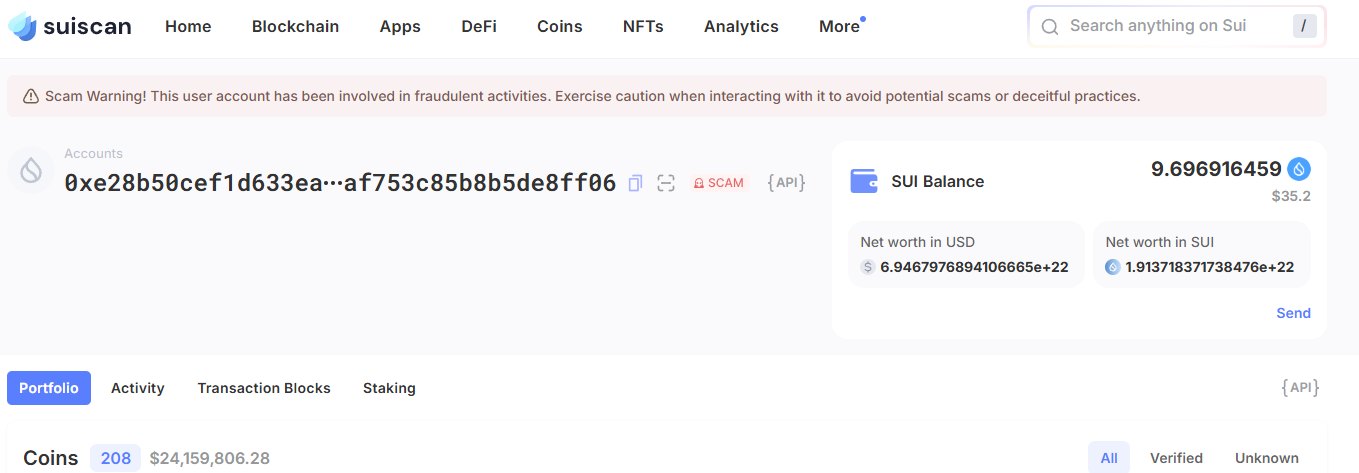
At the moment, one of the hacker’s Sui-accounts remains 208 different coins worth about $24 million. On other — 6 more tokens worth $87 million. No activity (addresses are frozen).
The hacker converted the rest of the stolen assets into ETH, and the tokens are currently stored in two Ethereum wallets: on alone $54.4 million, by other — $8.8 million.
What about the victims’ money?
Cetus is working with Sui’s security team and several audit partners to re-examine the updated contracts and conduct a comprehensive audit. Only after full validation will the gradual reactivation of CLMM pools and services begin. The team also proposed a plan to recover frozen assets. The protocol community will vote on the update at the leadership level. If approved, it allows the return of frozen assets from the wallets of criminals without their signature. The recovered funds will be protected in a multi-signature wallet jointly controlled by Cetus, OtterSec, and Sui Foundation.
Voting started on May 27 and will last until June 3. In order for it to be successful, more than 50% of the total number of tokens must participate and be approved by a majority.
Sui Foundation has provided a secured loan to Cetus to compensate users for 100% of their losses. The Sui Foundation has also allocated $10 million for ecosystem security, funding audits, bug fixes, and official verification tools to prevent future abuse.
In addition, despite the incident, all xCETUS rewards have been awarded and distributed this week as they were registered before the pools were shut down. However, next week, xCETUS rewards will be temporarily suspended due to the suspension of the CLMM pools. xCETUS is a special token that users receive by staking the main CETUS token on the Cetus Protocol platform. It serves as a management and reward token.
What’s next?
Those affected will have to wait until June and the results of the vote. The Cetus team promised to strengthen security and improve risk control:
- use tools such as Blockaid to monitor in real time and identify and respond to threats and vulnerabilities.
- Improve configurations for risk management and controlled limitation of asset flows.
- Source code for smart contracts with higher test coverage.
- Public reporting of code coverage metrics.
- Audits before general releases, after major code changes, and when key TVL milestones are reached
 Shows how many cryptocurrencies are blocked in the smart contracts of a particular DeFi project. .
Shows how many cryptocurrencies are blocked in the smart contracts of a particular DeFi project. . - Improved bug bounty program for white-hat hackers.

Spelling error report
The following text will be sent to our editors: