
Researchers have discovered a serious vulnerability in a series of popular printers that exposes administrator passwords by default. Worse, it cannot be fixed through the firmware of existing printers.
The affected models include 689 Brother printers and some Fujifilm (46 models), Toshiba (2), Ricoh (5), and Konica Minolta (6).
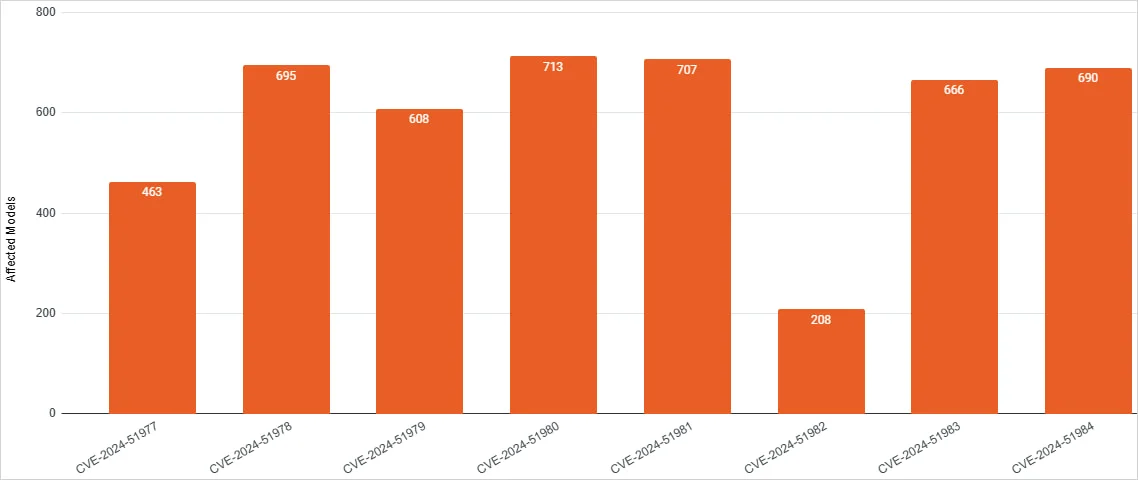
Vulnerability CVE-2024-51978 — is part of a set of eight vulnerabilities that Rapid7 researchers discovered (via Bleeping Computer) during an ongoing investigation of Brother equipment. It can be used to determine the administrator password, gain control of the printers, and execute remote code to disable the device and further penetrate other parts of the network to which it is connected.
The default password in the respective printers is generated at the production stage using a special algorithm that uses the serial number of the device.
According to Rapid7’s analysis, the password generation algorithm performs an easily reversible process:
- The first 16 characters of the serial number are taken;
- Next, 8 bytes are added from the statistical table «salts»
 Salt in cryptography is random or predefined data that is added to a password or other information before hashing to make it more difficult to crack, in particular through pre-prepared rainbow tables.;
Salt in cryptography is random or predefined data that is added to a password or other information before hashing to make it more difficult to crack, in particular through pre-prepared rainbow tables.; - The result is hashed using SHA256
 SHA-256 (Secure Hash Algorithm 256-bit) — is a cryptographic hash function that converts any input data (text, file, etc.) into a fixed 256-bit (32-byte) hash, or, more simply, into a unique digital «fingerprint» data.;
SHA-256 (Secure Hash Algorithm 256-bit) — is a cryptographic hash function that converts any input data (text, file, etc.) into a fixed 256-bit (32-byte) hash, or, more simply, into a unique digital «fingerprint» data.; - The hash is encoded in Base64
 Base64 — is a way of encoding data into text form that allows you to transmit any (even binary) data through text channels, for example, on the web, email, or JSON.;
Base64 — is a way of encoding data into text form that allows you to transmit any (even binary) data through text channels, for example, on the web, email, or JSON.; - The first eight characters are taken from the string and some letters are replaced with special characters.
Attackers can gain access to the target printer’s serial number using various methods or by exploiting CVE-2024-51977, then use an algorithm to generate a default administrator password and log in as administrator to do whatever they want — including accessing stored scanned files, address books, or collecting credentials.
«While all flaws have been fixed in firmware updates provided by the affected vendors, the case of CVE-2024-51978 is challenging from a risk management perspective. The vulnerability is rooted in the password generation logic used in hardware manufacturing, and therefore any devices manufactured before it was discovered will have predictable passwords unless users change them», — Bleeping Computer writes.
What should users do?
The first step is to change the default administrator password and then apply a firmware update. In general, it is recommended to limit access to the printer’s administrative interfaces via insecure protocols and external networks.
Each of the manufacturers of the affected devices has issued their own instructions for this purpose:

Spelling error report
The following text will be sent to our editors: