
In the NPM package repository, pieces of malicious code were found that use Ethereum smart contracts to download malware. Users of public libraries of blockchain-related code may become victims of the attackers. Similar actions were previously attributed by Binance to North Korean hackers.
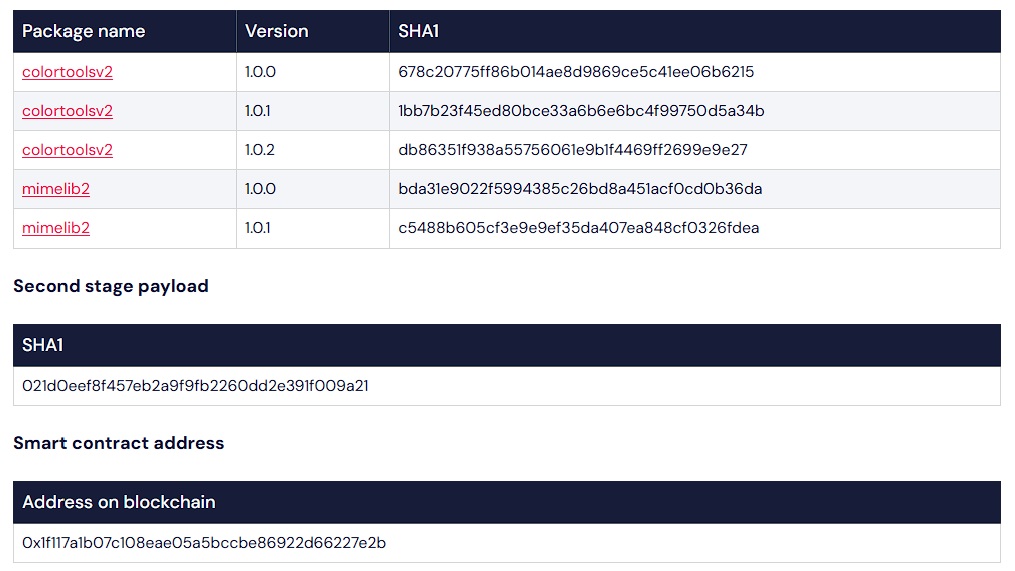
Two Node Package Manager (NPM) libraries called colortoolsv2 and mimelib2 were almost identical, as they contained two files, one of which ran a script that downloaded the second half of the malware via the Ethereum smart contract.
NPM packages are reusable open source collections.
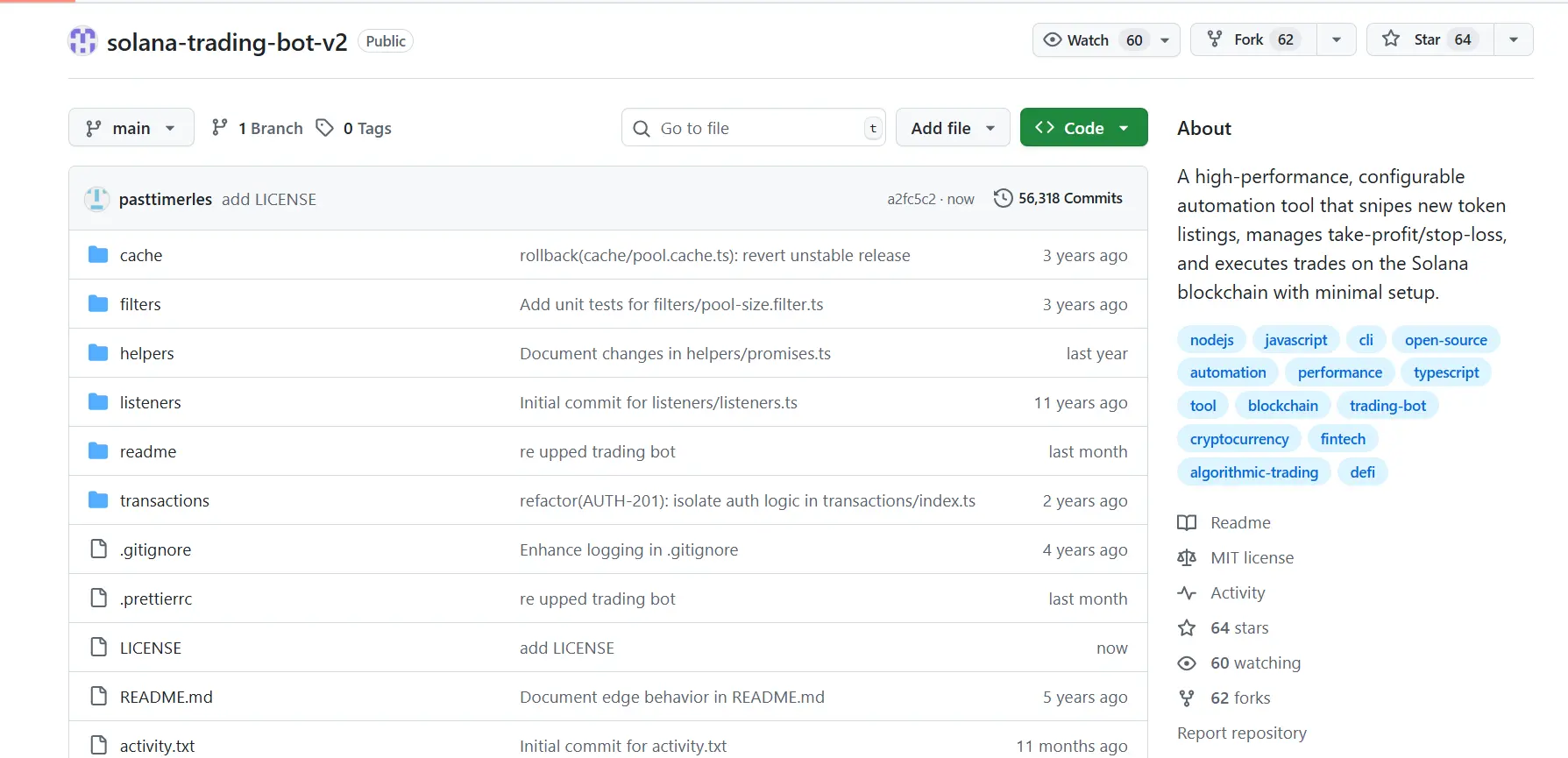
The use of Ethereum smart contracts to host URLs with malicious commands that download second-stage malware is something new. Both packages were just the tip of the iceberg, as more poisoned packages were discovered on GitHub. They are related to the above colortoolsv2. The authors of the code turned out to be fake, and the actual number of commits was overestimated. There are thousands of them, and this number is increasing by several thousand every day, indicating that the attackers have created an infrastructure for sending commits automatically.
Such public packages are often used by developers to develop trading or sniping bots.
Code package poisoning is a new area of attack against the crypto industry. It is the DPRK hackers, including the well-known Lazarus, who have been concentrating on this area for the past two to three years. North Korean hackers are believed to be responsible for the theft of 61% of all cryptocurrencies in 2024, which amounted to $1.3 billion.
Source: ReversingLabs

Spelling error report
The following text will be sent to our editors: