
It turns out that artificial intelligence, despite its gigantic knowledge base, may not be too inventive in choosing a password — as happened in the case of the McDonald’s chatbot.
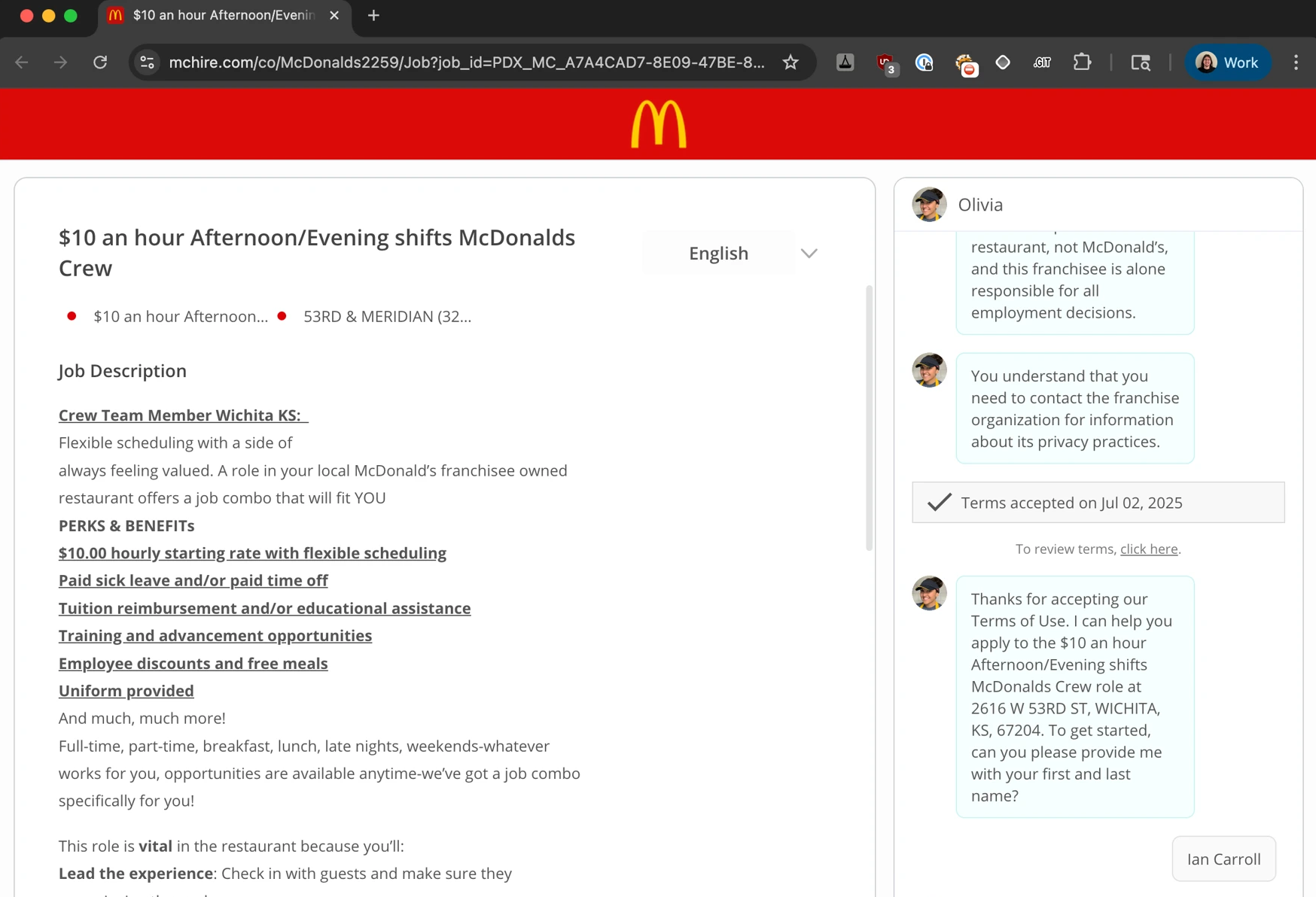
If you’re planning to apply for a job at McDonald’s, there’s a good chance you’ll have to talk to Olivia, the bot that took over the company’s HR manager.
Olivia screens candidates, asks for their contact information and resume, and sends them to a personality test, sometimes driving people «crazy» by misinterpreting answers to the simplest questions. However, this is not the main problem — the bot runs on the Paradox.ai platform, which turned out to have absurdly basic security flaws.
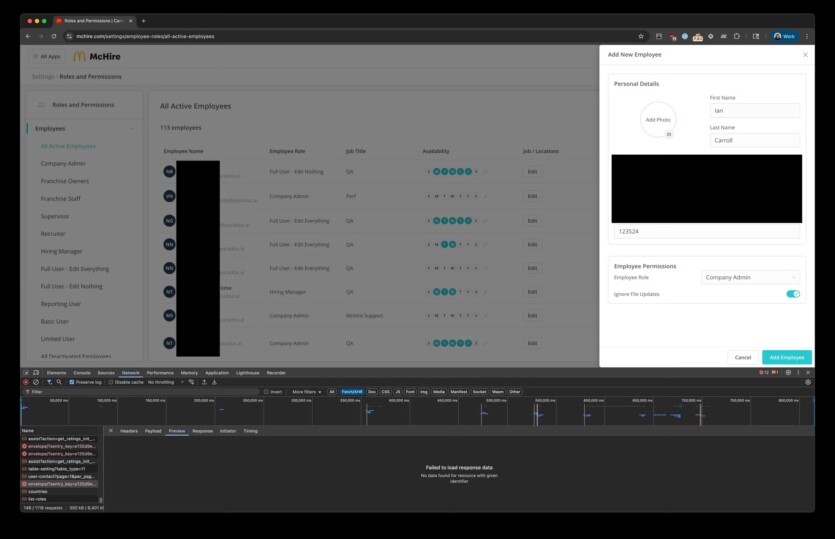
On Wednesday, cybersecurity researchers Ian Carroll and Sam Curry reported that they had found simple methods to hack into the server side of the chatbot platform on McHire.com, a website used by many McDonald’s franchisees to process job applications. As it turned out, the administrative interface accepted standard username and password «123456», while the internal API had an IDOR (Insecure Direct Object Reference) vulnerability that allowed access to any chats or contacts.
The data, according to the researchers, contains up to 64 million records, including the names, email addresses and phone numbers of the candidates.
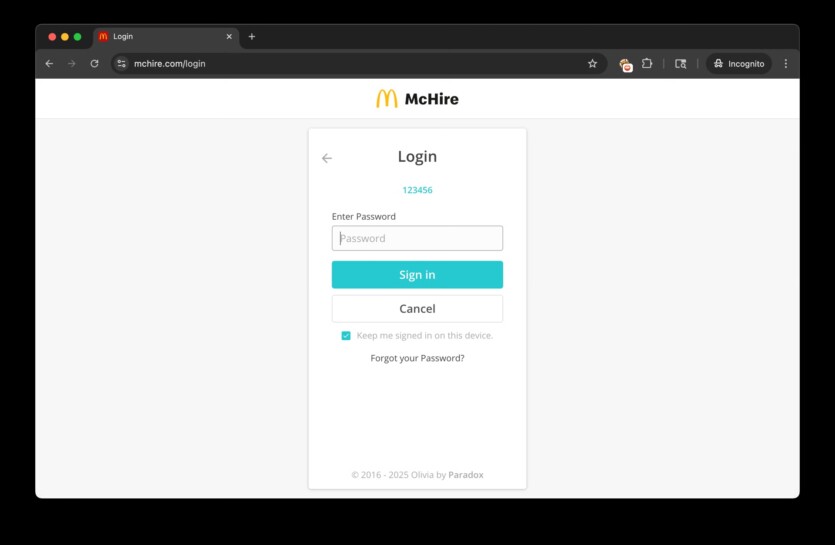
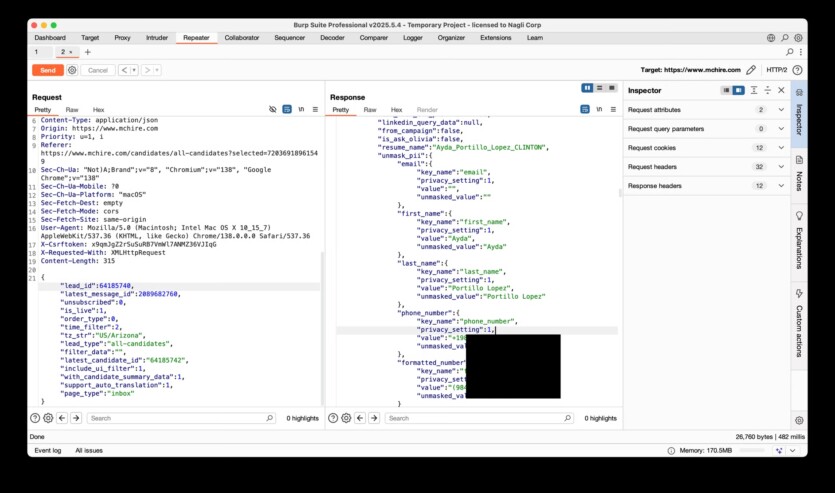
Carroll says he decided to check out the platform because he was interested in McDonald’s decision to test employees through a chatbot, which seemed like a somewhat dystopian hiring process.
«I just thought it was a pretty uniquely dystopian process compared to the normal hiring process, right? And that’s what made me want to look into it more,» Carroll says. «So I started applying for jobs, and within 30 minutes, we had full access to virtually every application that McDonald’s had ever received over the years».
Paradox.ai published a blog post with Carroll and Curry’s report, noting that it was «only a portion of the records» and they were not available to «any third party» except the researchers. The company added that it was introducing a bounty program for vulnerability disclosures.
McDonald’s pleaded guilty to Paradox.ai in a statement:
«We are disappointed with this unacceptable vulnerability in the third-party vendor Paradox.ai. As soon as we learned about the issue, we immediately had it fixed. This happened the same day the issue was reported. We take our cybersecurity obligations seriously and will continue to hold our third-party vendors accountable for meeting our data protection standards».
Earlier, we told you about an enterprising IT professional who worked at four AI startups simultaneously until managers did not discover that they were hiring the same personand how students bypass AI detectors… with artificial intelligence — because they mark real texts as generated.

Spelling error report
The following text will be sent to our editors: