
The US Federal Bureau of Investigation (FBI) has officially stated that Bybit hack for $1.5 billion linked to the North Korean hacker group Lazarus (also known as TraderTraitor) and identified the incident as a state-sponsored cyberattack aimed at laundering assets across multiple blockchains. The FBI called for blocking the hackers’ transactions to prevent further money laundering (the document contains the following addresses).
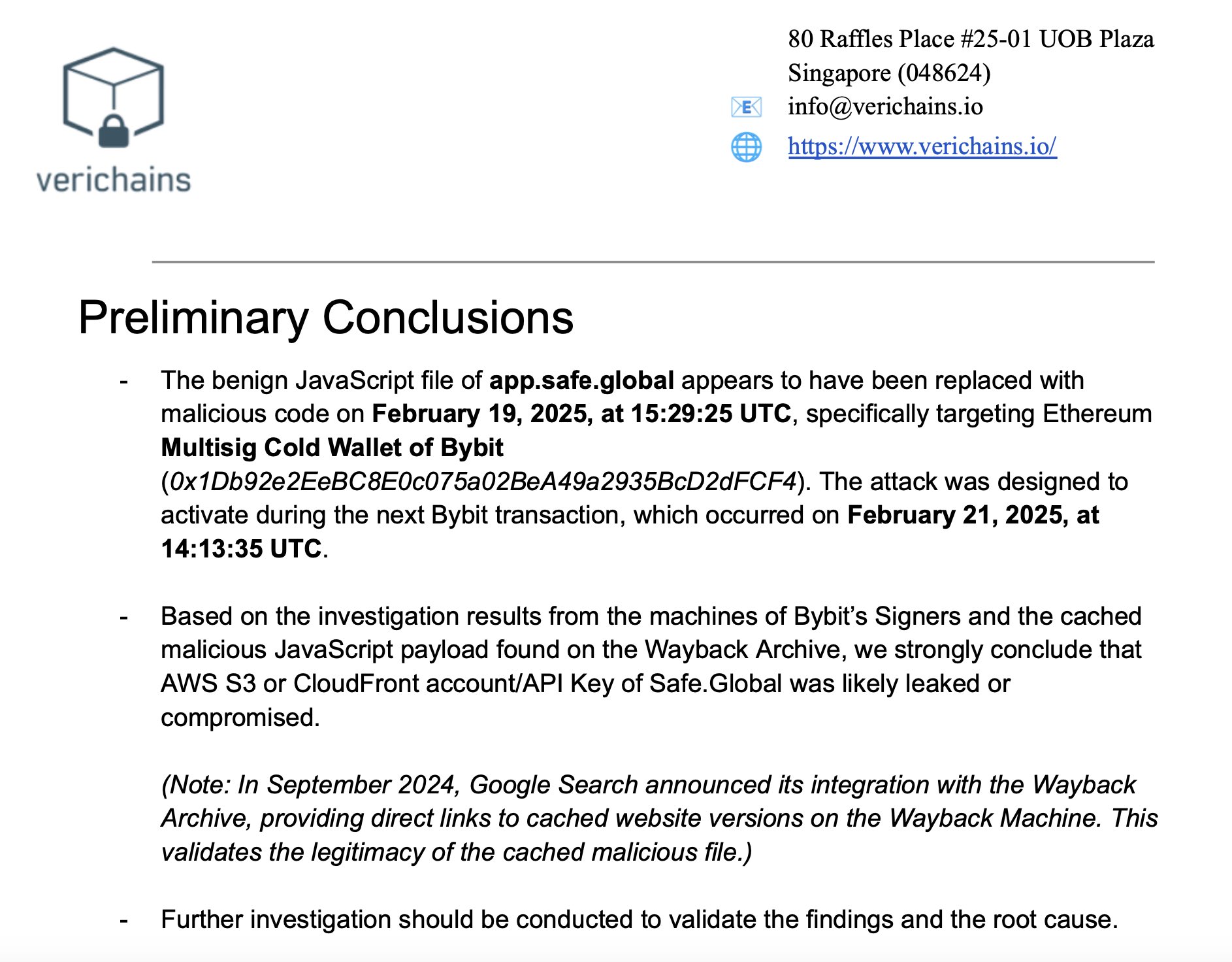
The Bybit crypto exchange also published its own investigation results. The author of the report, VeriChains, determined that the malicious code (a JavaScript file was replaced) was introduced on February 19, 2025, and activated on February 21 during a Bybit transaction. This was a routine operation that transferred funds from a multisig cold wallet (offline storage system) of Ethereum — to a hot (software) wallet intended for daily trading operations.
The attack was carried out through a compromised account or a leaked API key of infrastructure providers for Bybit: AWS S3 or CloudFront by Safe.Global. The malware cache was found thanks to the Wayback Machine.
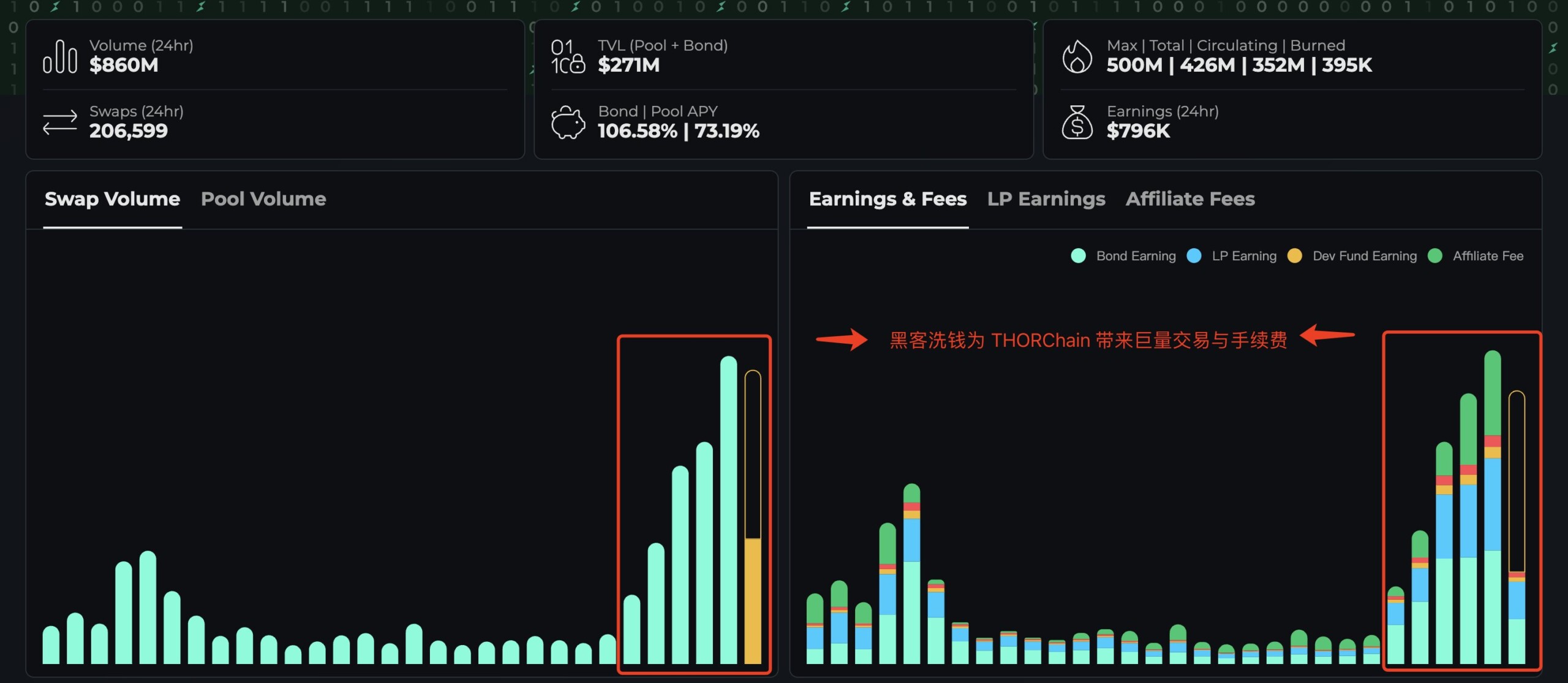
As a result of the Bybit hack, the THORChain platform, which the hackers used for money laundering, also benefited. The volume of transactions increased to $2.91 billion, and $3 million was received in processing fees within 5 days. Before the hackers started laundering stolen assets, the average daily transaction volume of THORChain was about $80 million.
Nine Realms engineer, developer of the THORChain core, performed in defense of the protocol. Pluto (9R) acknowledged that illegal funds were being transferred through THORChain, but added that the team helped to implement screening services.

Spelling error report
The following text will be sent to our editors: